We live in a world where the internet influences every facet of our lives. From e-commerce to banking, our personal data is susceptible to hackers. If you are not careful, you can find yourself in a position where your entire savings has been wiped out through hacking.
While you do not need to be a tech Geek to understand the scope of hacking, some basic information on the different types of attacks used by hackers can go a long way in keeping your personal data safe.
Phishing
Hackers use phishing malware to get personal data from you. The most common method for this is when you are sent an email – often looks legitimate – and are asked to download a certain file. The reason most people click on this attachment is that they are designed to be very catchy. The hackers have learned a thing or two about human behavior especially curiosity. They often use this trick to extract sensitive information from you.
You may also be directed to log in to another website. The hackers will then phish out the information you have keyed in. To prevent phishing attacks, your company can deploy the BestVPN.com. This enables your company to create a private secure network for sending and receiving sensitive information.
Malware
Malware are prevalent, and it is hacker’s way to gain access to your computer and install harmful software. The malware can either be a virus of ransomware. The hackers will use creative ways to cause you to click their file and therefore initiate the download process. Malware can be extremely dangerous and even cause your computer to crash. While the malware on your computer it will often send confidential information to the hackers. You can avoid malware by installing an antivirus or by being careful when opening suspicious emails and applications.
Common types of malware include:
- File Infectors: this attaches to executable code. The moment you open the .exe file the malware is installed to your computer. Some of the files may share the same qualities with a genuine .exe file.
- Macro viruses: these are often associated with excel and word files. The virus will come with the file and the moment you execute the macro the virus takes control of the application.
- Trojans: they are often confused with viruses, but the main difference is that Trojans do not replicate themselves like viruses. They also can create backdoors for hackers to use. The Trojan can be hard to detect because it hides behind vital programs.
Denial of Service (DoS)
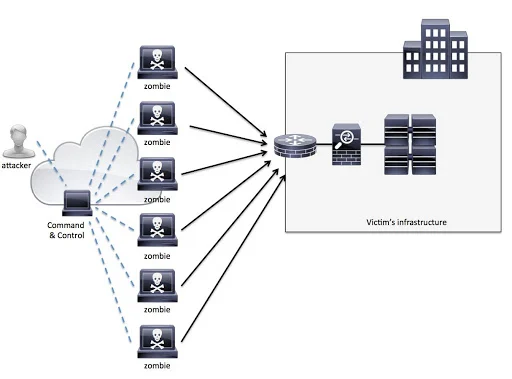
In recent years this has become a common form of cyber-attacks. The most common form of DoS attacks is when the hackers flood a company’s website with requests that is becomes almost impossible to serve the legitimate customers. There instances where the overflow in traffic is legitimate – for example when there is some breaking news. Differentiating the legitimate customers from the hackers can be a herculean task. Their instances where the hackers will use various computers with different IP addresses and this can prove a challenge to find the source of the attacks. While the attackers do not directly profit from the attack the times the company’s website is offline can cause serious damage when it comes to sales. In some instances, the hackers use a DoS attack as a conduit for other cyber-attacks.
Passwords Attack
Today we need a password for almost all online transactions. The attackers use several methods to snoop online for passwords. The easiest passwords to steal are those from unencrypted data sources. Hackers can also engage is some guessing work to get a password. Most people have created passwords using their names, children’s names, home addresses, and other personal information. These passwords are easy to guess once someone has access to your personal information. In a dictionary attack, the hackers use a dictionary for some of the common passwords to gain access to your account. Have different characters for your accounts and ensure that you log out from a website that initially required you to key in a password.
SQL Injection Attack

Through SQL companies can store large amounts of data in their servers. It stands for Structured Query Language. Since data is very sensitive hackers use this technique to get access to crucial information. They will often send a malicious code to compel the servers to give them vital information. Some of the information targeted include passwords, credit card details, user names among others. SQL injection attacks have often been used with ASP or PHP applications because they use old interfaces.
Cross-Site Scripting (XSS)
These kinds of attacks target the website users. Unlike the SQL injection attack that will target the database in this case the hackers will send a malicious code to a website and this code will capture information been sent by the website visitors. This code can be a JavaScript that pops up when you are log in to the site. Through cross-site scripting people visiting a website can lose their personal information and this damages the credibility of the website.
Session Hijacking
While you cannot see it, anytime you are using a website there is often a back and forth sharing of information between the website and the servers. You will request information which will be transmitted to the servers, and after sometime you should have what you requested displayed on the website. Session hijacking takes place when hackers acquire a unique session ID that has been allocated to your computer by the remote server. When this ID is hijacked the hackers send and receive information like your computer. Through session hijacking, the hackers can intercept any information that is been sent between your computer and the remote server.
Conclusion
Losing personal data can be painful and costly for companies. That is why you need to deploy the very best cyber-security strategies to keep your data safe and secure. Hackers over time come up with creative ways to deploy cyber-attacks. VPN is one way to protect your private data sharing system across the internet.








