WhiteHat has disclosed a critical security vulnerability in Apple’s Safari browser that could allow hackers to extract personal information from the OS X address book.
“Right at the moment a Safari user visits a malicious website, even if they’ve never been there before or entered any personal information, [it] can uncover their first name, last name, work place, city, state and email address,” WhiteHat CTO Jeremiah Grossman wrote in an official blog post.
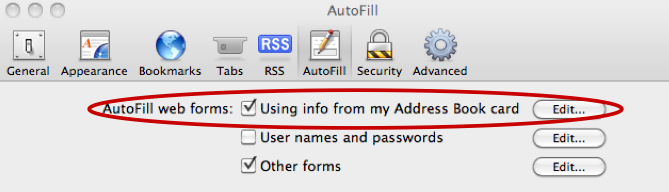
“Safari v4 & v5, with a combined market browser share of 4% (~83 million users), has a feature (Preferences > AutoFill > AutoFill web forms) enabled by default. Essentially we are hacking auto-complete functionality.”
According to Grossman, malicious websites would likely operate by surreptitiously extracting Address Book card data and dynamically creating form text fields with matching names.

The site would then simulate A-Z keystroke events using JavaScript.
“When data is populated, that is AutoFill’ed, it can be accessed and sent to the attacker. [Now], this entire process takes mere seconds and represents a major breach in online privacy,” explained Grossman.
“The [breach] could be further leveraged in multistage attacks including email spam, (spear) phishing, stalking and even blackmail if a user is de-anonymized while visiting objectionable online material.”
However, Grossman emphasized that any AutoFill data beginning with a number would remain off limits to a malicious website.
“For some reason, the data [will] not populate in the text field. Still, such attacks could be easily and cheaply distributed on a mass scale using an advertising network where likely no one would ever notice because it’s not exploit code designed to deliver rootkit payload.
“In fact, there is no guarantee this has not already taken place. What is safe to say is that this vulnerability is so brain dead simple that I assumed someone else must have publicly reported it already, but exhaustive searches and asking several colleagues turned up nothing.”
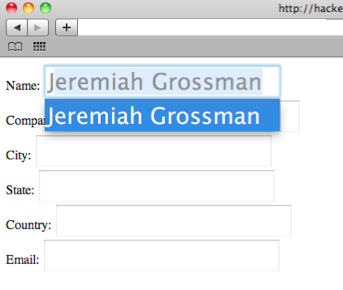
Unsurprisingly, Grossman revealed that Apple had yet to seriously address the issue.
“I figured Apple might appreciate a vulnerability disclosure prior to public discussion, which I did on June 17, 2010 complete with technical detail. A gleeful auto-response came shortly after, to which I replied asking if Apple was already aware of the issue.
“I received no response after that, human or robot. I have no idea when or if Apple plans to fix the issue, or even if they are aware, but thankfully Safari users only need to disable AutoFill web forms to protect themselves.”






