The air at HP’s Security Summit this month was charged with a different kind of urgency. Between the polished keynotes and the hushed conversations in the hallways, one theme became terrifyingly clear: the era of “dumb” malware is ending. I was briefed on a shift that security professionals have feared for years—the graduation of Agentic AI from theoretical malware trials to active, autonomous deployments in the wild.
But while Agentic AI represents the future, a massive, silent predator is already here. HP researchers shared a startling statistic: a specific wave of sophisticated information stealing malware has now quietly infected an estimated 300,000 PCs. This isn’t just about stolen passwords anymore; this campaign is surgically targeting active session cookies, a technique that renders your dual-factor authentication (2FA) useless and allows hostile actors to empty bank accounts without ever needing your OTP code.
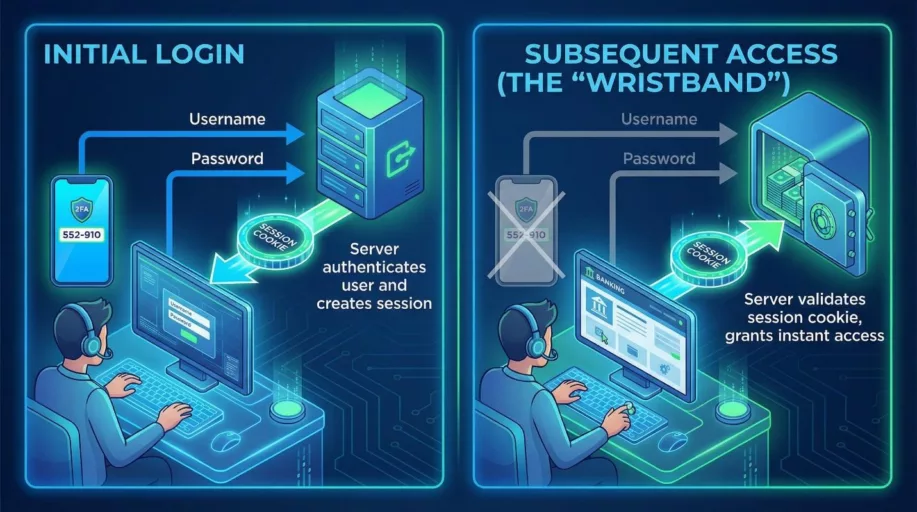
The Digital Wristband: Understanding Session Cookies
To understand this threat, we have to look at how the modern web keeps us logged in. When you log into your bank or email, the server checks your credentials (username, password and 2FA code). Once verified, it doesn’t ask for your ID every time you click a new page. Instead, it issues a session cookie.
Think of this cookie like the paper wristband you get at a concert or a club. The bouncer (the login screen) checks your ID once at the door. After that, as long as you are wearing the wristband, you can walk in and out, order drinks and access VIP areas without showing your ID again. In the digital world, this “wristband” is a small text file stored in your browser. It tells the bank, “This user has already been authenticated. Let them in.”
The Invisible Invader: Information Stealing Malware
Information stealing malware (or “Infostealers”) is a category of malicious software designed to harvest data from an infected machine. Unlike ransomware, which announces its presence with a locked screen and a demand for payment, infostealers are designed to be ghosts. They want to remain undetected for as long as possible to siphon off data.
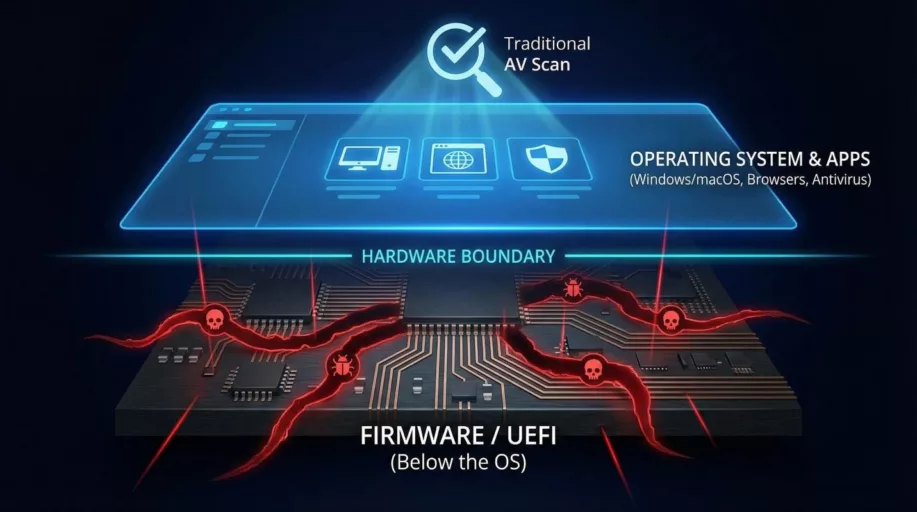
What was particularly alarming in the summit briefing was the discussion of how some of these modern threats are achieving persistence “below the operating system.” This refers to malware that infects the UEFI (Unified Extensible Firmware Interface) or the BIOS—the fundamental software that boots your computer before Windows or macOS even starts.
When malware resides here, it is essentially invisible to traditional antivirus software running within the operating system. You can wipe your hard drive, reinstall Windows, and think you’re safe, but the malware survives in the motherboard’s firmware, reinstalling itself the moment you reboot. This makes it incredibly difficult to eliminate, requiring specialized tools and sometimes even hardware replacement to eradicate.
The Heist: Bypassing Dual-Factor Authentication
The 300,000 PCs identified by HP are essentially open doors for cybercriminals, primarily because of how this malware targets those session cookies we discussed.
Here is the frightening reality: You can have the strongest password in the world and the most sophisticated 2FA app, but if an attacker steals your active session cookie, none of that matters.
Recall the wristband analogy. If a thief steals your physical wristband at the club, they can walk right past the bouncer. The bouncer doesn’t ask for their ID because the wristband is the proof of verification. Similarly, when Infostealer malware exfiltrates your active session cookies and sends them to a hostile actor, that actor can load the cookies into their own browser.
To the bank’s server, the attacker looks exactly like you. They appear to be coming from an authenticated session. They don’t need your password. They don’t need your fingerprint. They don’t need the SMS code sent to your phone. They are already “logged in” because they possess the digital proof that you completed those steps. From there, emptying a bank account or stealing corporate data is trivial.
Agentic AI: The New Force Multiplier
Compounding this threat is the rise of Agentic AI. At the summit, experts detailed how AI is moving beyond generating phishing emails to becoming the malware’s brain.
Traditional malware follows a rigid script: Infect > Steal > Send. Agentic AI malware is different. It has goals and autonomy. It can “reason” about its environment. If it encounters a security tool, it doesn’t just crash; it might pause, change its behavior, or look for a different vulnerability to exploit. It can intelligently parse the data it finds, deciding on the fly that a session cookie for a corporate admin portal is worth more than a personal Netflix login, and prioritizing its exfiltration accordingly.
Mitigating the Threat: The Human Element
While the technology is terrifying, one simple behavioral change can partially mitigate the risk of session hijacking: Log out.
Most of us simply close the browser tab when we are done with our banking or sensitive work. This often leaves the session cookie active on your drive until it expires (which can take hours or days). By clicking the actual “Log Out” or “Sign Off” button, you are telling the server to invalidate that specific “wristband.” Even if malware steals the cookie afterwards, it will be useless—a torn wristband that the bouncer won’t accept.

Hardware-Enforced Defense: The HP Wolf Security Approach
Behavioral changes are necessary, but they aren’t enough against malware that lives below the OS. This is where the hardware-based security discussed at the summit—specifically HP Wolf Security—becomes critical.
Standard antivirus fights on the same playing field as the malware (the OS). HP changes the battlefield.
- HP Sure Click uses micro-virtualization. When you open an email attachment or click a link, it doesn’t open in the main operating system. Instead, it opens in a disposable, hardware-enforced “micro-VM.” If that link contains the Agentic AI malware or an infostealer, it detonates inside this digital container. The malware thinks it has infected your PC, but it is actually trapped in a virtual jail cell. When you close the window, the cell is destroyed—along with the malware.
- For threats targeting the firmware (below the OS), HP uses a secure Hypervisor and technologies like Sure Start. This creates a hardware root of trust. The PC checks its own BIOS/UEFI code for integrity every time it boots. If it detects that the firmware has been tampered with (by a rootkit, for example), it refuses to run the compromised code and automatically heals itself by reloading a “golden copy” of the safe firmware from a dedicated, isolated chip.
Wrapping Up
The briefing at HP’s Security Summit served as a stark warning: the threat landscape has evolved. With 300,000 PCs acting as silent informants and Agentic AI actively hunting for our digital keys, reliance on standard software defenses is no longer sufficient. The combination of deep-seated firmware malware and session hijacking requires a new defense strategy—one that combines vigilant user behavior, like actively closing sessions, with robust, hardware-enforced isolation that traps threats before they can dig in.
Here are some additional resources if you want to read up on these threats and how to mitigate them:
- HP Wolf Security Threat Insights: Comprehensive reports on how isolation technology mitigates threats that evade traditional detection. HP Wolf Security Reports
- Understanding Session Hijacking: An overview of how session cookies are compromised. CISA.gov – Cyber Threats
- Agentic AI Risks: Insight into the shift toward autonomous AI threats. SecurityWeek on Agentic AI








