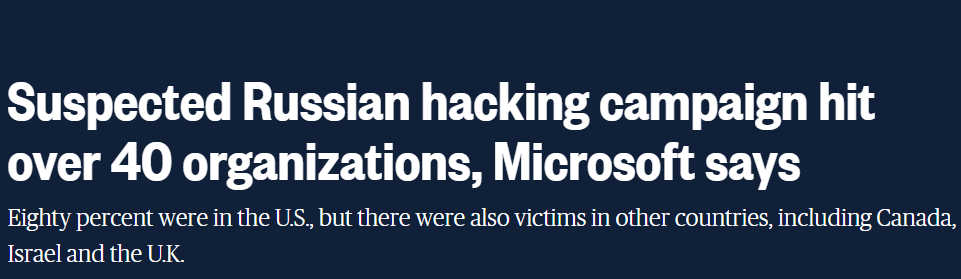
Over 40 organizations have been compromised by the suspected Russian cyber breach campaign. This was revealed by Microsoft in a blog post last Wednesday. Officials say that the hacking campaign has been going on since March, however, the illegal activities have only been discovered last week when multiple federal agencies got hit. 80% of those affected by the breach were from the U.S while the rest were from Canada, Mexico, Belgium, Spain, the United Kingdom, Israel and the United Arab Emirates. Microsoft announced that they are working with cybersecurity company, FirmEye as an investigative partner. Although both were victims of the malware, they have already isolated and removed a vulnerability in the system. Currently, investigations are still ongoing to assess the extent of the damage.
Read: Attack on SolarWinds’ Software Vulnerabilities Linked to Recent Hacking Incident in the U.S
CNN: Microsoft had been compromised as well but it has “isolated and removed” a vulnerability in its systems

CNN shared Microsoft said that 80% of the victims are in the US while the rest are in seven other countries: Canada, Mexico, Belgium, Spain, the United Kingdom, Israel and the United Arab Emirates.
Microsoft’s analysis represents the clearest and most specific assessment yet of the scope of the damage caused by the hacking campaign, which was secretly conducted through a third-party software program sold by SolarWinds, an IT management firm.
Earlier Thursday, Reuters reported that Microsoft had been compromised as well. Microsoft said it has “isolated and removed” a vulnerability in its systems tied to third-party software that had facilitated a suspected Russian hacking campaign.
NBC News: The breadth of the campaign has been an open question because it had the opportunity to infect a staggeringly wide array of victims.
According to NBC News, in March, the hackers were able to send poisoned software updates to all SolarWinds customers who used versions of its popular Orion platform, giving them a foothold into victims’ systems.
While many victims were government agencies, companies that contract with governments or think tanks and information and technology companies were also frequently hit, Microsoft found.
Microsoft’s statement is the first to provide a detailed estimate of how widespread the hack is. While the company doesn’t have total visibility into the hacking campaign, it has significant insight thanks to governments and corporations’ use of Windows and its antivirus software, Defender.








